SOC

SOC Solution
This proposal outlines the design, implementation, and management of a Security Operations Centre (SOC) for [ your ORG ] leveraging Microsoft Azure. The SOC will provide real-time threat monitoring, Detection, Triage incident response, and compliance management.
S4Hana SD, SAP CRM, Fiori, ServiceNow, SAP solution manager, AfterShip Shipment Web application, PriceFX WebApplication
Objectives
- Provide 24/7 monitoring and Detection
- Provide L1, L2 support
- Enhance cybersecurity posture by performing periodic assessments.
- Enhance threat intelligence capabilities.
- Perform Threat Hunting (quarterly /annually).
SOC Architecture on Microsoft Azure
Key Components
Azure Sentinel (SIEM & SOAR) – Collects, detects, and responds to security incidents.
Microsoft Defender XDR– is a unified pre- and post-breach enterprise defence suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks. Microsoft Defender for Endpoint
- Microsoft Defender for Office 365
- Microsoft Defender for Identity
- C. Microsoft Defender for Cloud Apps
- Microsoft Defender Vulnerability Management
- Microsoft Defender for Cloud
- Microsoft Entra ID Protection
- Microsoft Data Loss Prevention
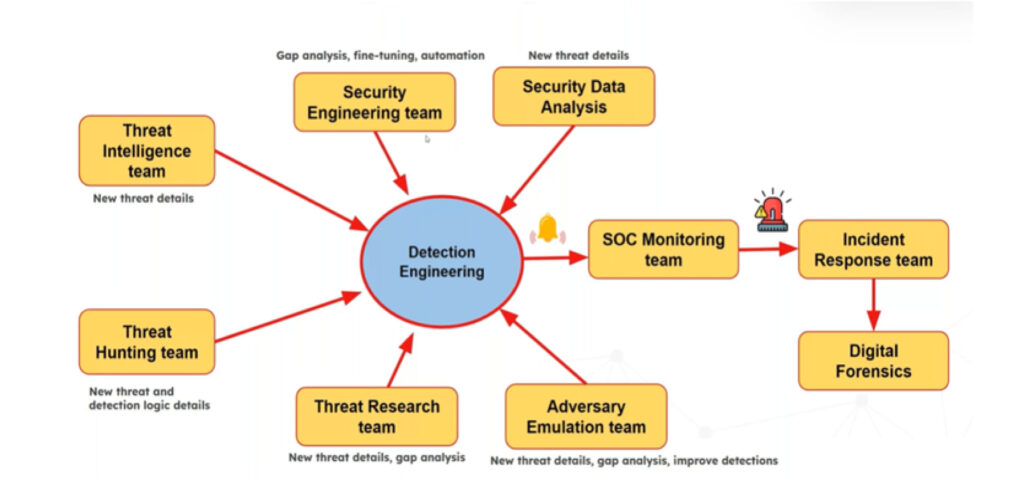
SOC Design Pattern
SOC Implementation Plan
Phase 1: Assessment & Planning
- Conduct security assessment security gap analysis.
- Identify the relevant logging/ingestion to SIEM(Sentinel)
- Define security monitoring policies and alert thresholds.
Phase 2: Deployment & Integration
- Deploy Azure Sentinel, configure data connectors
- Integrate with Defender solutions and third-party tools.
- Enable log collection from cloud, on-prem, and hybrid environments.
Phase 3: SOC Operations & Incident Response
- Set up SOC workflows/SOPs for incident detection, analysis, and response.
- Implement playbooks and automated responses with SOAR.
- Monitor security incidents 24/7.
- Daily provide Threat advisories as per the customer domain.
Phase 4: Optimization & Continuous Improvement
- Conduct regular security drills and testing.
- Generate reports for compliance (ISO 27001, NIST, GDPR, etc.).
- Optimize threat detection rules and incident response strategies.
Next Steps
- Approve the SOC proposal and finalize scope.
- Schedule a kick-off meeting for assessment.
- Deploy initial security monitoring and conduct tests.
Benefits to Clients
- Proactive Threat Hunting: Staying ahead of Threat actors before they penetrate customer environment
- Precise and sharp Threat intelligence catering to customer environment
- Cost-Efficient & Scalable: Pay as you go model.
- Seamless Integration: Works natively with Microsoft security solutions.
- Compliance & Reporting: Ensures adherence to industry security standards like ISO/IEC27001, HIPPA, PCI DSS etc.
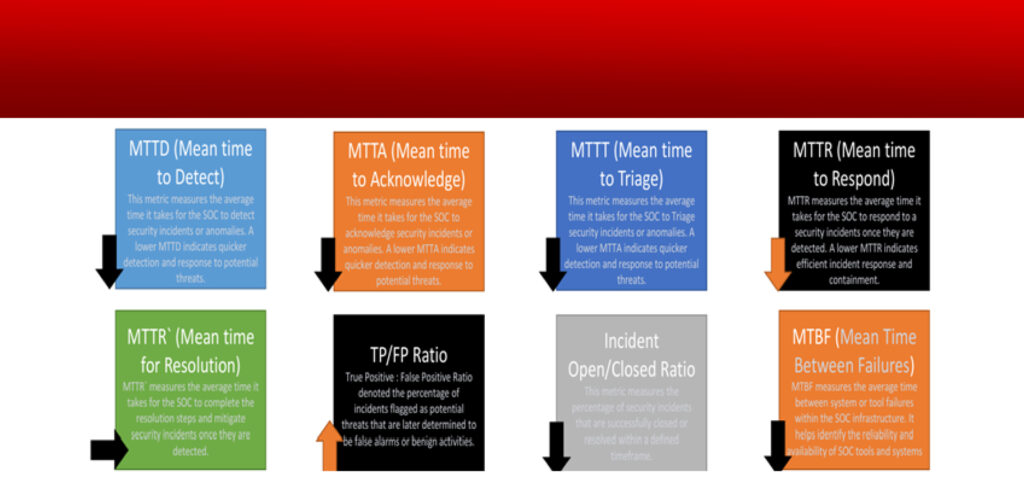
SOC KPIs